Stay informed with the latest insights, best practices, and expert analysis on cybersecurity, cloud security, and emerging threats.
Artificial Intelligence is rapidly transforming digital ecosystems across finance, healthcare, defense, and cloud computing. However, the expansion of...
Read More
Modern America runs on software. From energy grids and hospitals to financial systems and defense networks, digital infrastructure depends on complex ...
Read More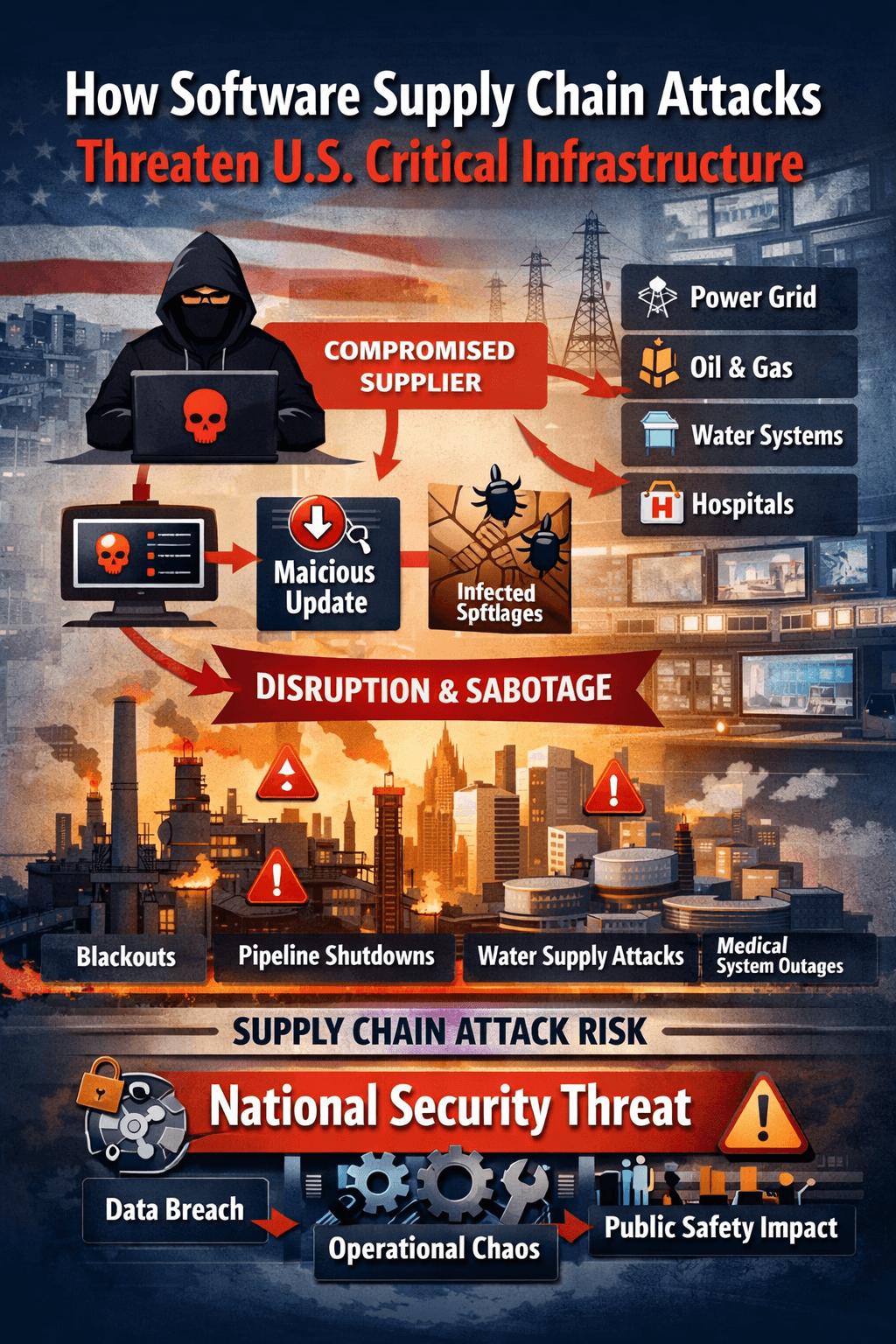
Software has become the connective tissue of U.S. critical infrastructure. Power generation and transmission, oil and gas pipelines, water treatment, ...
Read More
Supply chain attacks succeed because they exploit trust and scale.
Read More
As enterprises increasingly rely on cloud services to store, process, and manage their data, protecting sensitive information has become more critical...
Read More
Ransomware has emerged as one of the most significant cybersecurity threats of the modern era. From crippling hospitals and government agencies to tar...
Read More
As organizations continue to migrate to the cloud, securing cloud infrastructure has become a critical priority. The shared responsibility model means...
Read More
Zero-day vulnerabilities represent one of the most dangerous and unpredictable threats in cybersecurity. Unlike known security flaws that can be patch...
Read More
Artificial Intelligence is fundamentally transforming cybersecurity. As digital systems expand across cloud platforms, mobile devices, critical infras...
Read More
Machine learning has emerged as one of the most transformative technologies in modern cybersecurity. As cyber threats increase in volume, sophisticati...
Read More
Ethical hacking is one of the most important and misunderstood areas of cybersecurity. While the term “hacking” often carries negative connotations, e...
Read More